Local Municipality Impersonation to Steal Data and Funds
 The NJCCIC received reports of threat actors impersonating multiple New Jersey local municipalities to steal sensitive data and funds and exploit public trust. Threat actors take advantage of residents who interact with their local municipalities regularly and are more likely to trust communications appearing to be official. They pose as local officials and contact residents through unsolicited communications to demand information or money using threats and deceptive tactics such as stolen branding and logos, unofficial or spoofed email addresses and phone numbers, and fake documents.
The NJCCIC received reports of threat actors impersonating multiple New Jersey local municipalities to steal sensitive data and funds and exploit public trust. Threat actors take advantage of residents who interact with their local municipalities regularly and are more likely to trust communications appearing to be official. They pose as local officials and contact residents through unsolicited communications to demand information or money using threats and deceptive tactics such as stolen branding and logos, unofficial or spoofed email addresses and phone numbers, and fake documents.
In the above example, threat actors impersonate a local municipality in an unsolicited email to create urgency and legitimacy by demanding additional payment to avoid delays in the bulk variance application approval process. The sender’s display name is “Planning Commission [local municipality name].” In the sender’s email address, the username is “planning-commission.[local municipality name]nj” with a “usa” domain name and .com top-level domain (TLD), unlike the official local municipality. The subject line displays “Settlement of Application Review and Approval Fee Invoice” and includes an attached Adobe PDF file.
The attached Adobe PDF file appears to be an official and legitimate invoice, but it contains stolen branding and logos in the watermark in the background and on the letterhead. The fraudulent invoice itemizes various fees due upon receipt. Unlike typical payment methods of checks or official portals, the remittance instructions in the invoice indicate payment is only through wire transfer, and the threat actors will provide those instructions upon request. If requested, the bank account information provided is not affiliated with the local municipality and may be linked to an out-of-state bank account. The threat actors further instruct their target to email them a signed copy of the invoice and the wire transfer payment receipt for confirmation. The invoice also states that this fee supports the administrative processing, legal evaluation, zoning compliance verification, and public notification procedures directly tied to the recipient’s application. If this fraudulent scheme is successful, the threat actors steal the funds and use the victim’s sensitive information and signature to commit identity theft, financial fraud, and other malicious activity.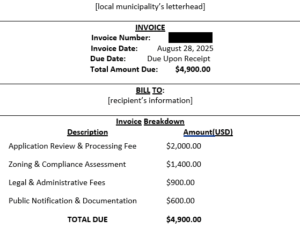
Recommendations
- Exercise caution with communications from known senders or legitimate platforms, especially unsolicited communications claiming you owe money.
- Be suspicious of any urgent demand for payment via wire transfer, gift cards, or cryptocurrency, as these payment methods are unusual and difficult to trace, reverse, and recover stolen funds.
- Confirm requests from senders via contact information obtained from verified and official sources before taking action, such as opening attachments or clicking links.
- Type official website URLs into browsers manually and only submit sensitive information on official websites.
- Keep systems and browsers up to date.
Report malicious cyber activity to the NJCCIC, the FBI’s IC3, and the FTC.
Source: NJCCIC Sept. 4 Bulletin.






Leave A Comment